
China-linked threat actors have breached several U.S. internet service providers in recent months as part of a cyber espionage campaign code-named Salt Typhoon.
The state-sponsored hackers aimed at gathering intelligence from the targets or carrying out disruptive cyberattacks.
The Wall Street Journal that experts are investigating into the security breached to determine if the attackers gained access to Cisco Systems routers, which are core network components of the ISP infrastructures.
A Cisco spokeswoman confirmed the investigation and said that “at this time, there is no indication that Cisco routers are involved” in the Salt Typhoon activity, the spokeswoman said.
The cyber campaign is attributed to the China-linked APT group Salt Typhoon, which is also known as FamousSparrow and GhostEmperor.
“Hackers linked to the Chinese government have broken into a handful of U.S. internet-service providers in recent months in pursuit of sensitive information, according to people familiar with the matter.” Wall Street Journal .
“The hacking campaign, called Salt Typhoon by investigators, hasn’t previously been publicly disclosed and is the latest in a series of incursions that U.S. investigators have linked to China in recent years. The intrusion is a sign of the stealthy success has had breaking into valuable computer networks in the U.S. and around the globe.”
China has long targeted global internet service providers and recent attacks are aligned with past operations linked to Beijing.
Intelligence and cybersecurity experts warn that Chinese nation-state actors have shifted from stealing secrets to infiltrate critical U.S. infrastructure, suggesting that they are now targeting the core of America’s digital networks.
The Salt Typhoon hacking campaign, linked to China, appears focused on intelligence gathering rather than crippling infrastructure, unlike the attacks carried out by another China-linked APT group called Volt Typhoon. Chris Krebs from SentinelOne suggested that the group behind Salt Typhoon may be affiliated with China’s Ministry of State Security, specifically the APT40 group, which specializes in intelligence collection. This group was publicly called out by the U.S. and its allies for hacking activities in July.
In July, Cisco fixed an actively exploited NX-OS zero-day that was exploited to install previously unknown malware as root on vulnerable switches.
Cisco addressed an NX-OS zero-day, tracked as CVE-2024-20399 (CVSS score of 6.0), that the China-linked group Velvet Ant exploited to deploy previously unknown malware as root on vulnerable switches.
Cybersecurity firm Sygnia observed the attacks on April 2024 and reported them to Cisco.
“Sygnia identified that CVE-2024-20399 was exploited in the wild by a China-nexus threat group as a ‘zero-day’ and shared the details of the vulnerability with Cisco. By exploiting this vulnerability, a threat group – dubbed ‘Velvet Ant’ – successfully executed commands on the underlying operating system of Cisco Nexus devices.” reads the report published by Sygnia. “This exploitation led to the execution of a previously unknown custom malware that allowed the threat group to remotely connect to compromised Cisco Nexus devices, upload additional files, and execute code on the devices.“
In August, Volexity researchers reported that a China-linked APT group, tracked as StormBamboo (aka Evasive Panda, Daggerfly, and StormCloud), successfully compromised an undisclosed internet service provider (ISP) in order to poison DNS responses for target organizations.
The threat actors targeted insecure software update mechanisms to install malware on macOS and Windows victim machines.
In mid-2023, Volexity discovered multiple malware infections affecting macOS and Windows systems within victim organizations. The company linked the attacks to StormBamboo APT group. Upon investigating the incidents, the researchers determined that a DNS poisoning attack at the ISP level caused the infection. The attackers altered DNS responses for domains related to software updates to deploy multiple malware families, including MACMA and POCOSTICK (MGBot). The attacker’s methods resemble those of DriftingBamboo, suggesting a possible connection between the two threat actors.
Daggerfly has been active for at least a decade, the group is known for the use of the custom MgBot malware framework. In 2023, Symantec identified a Daggerfly intrusion at an African telecom operator, using new MgBot plugins. This highlights the group’s ongoing evolution in cyber espionage tactics.
The Macma macOS backdoor was first detailed by Google in 2021 and has been used since at least 2019. At the time of discovery, threat actors employed the malware in watering hole attacks involving compromised websites in Hong Kong. The watering hole attacks used exploits for iOS and macOS devices. Attackers exploited the privilege escalation vulnerability CVE-2021-30869 to install Macma on macOS devices.
Macma is a modular backdoor that supports multiple functionalities, including device fingerprinting, executing commands, screen capture, keylogging, audio capture, uploading and downloading files.
Although Macma was widely used in cyber operations carried out by nation-state actors, it was not linked to a particular group.
“During one incident investigated by Volexity, it was discovered that StormBamboo poisoned DNS requests to deploy malware via an HTTP automatic update mechanism and poison responses for legitimate hostnames that were used as second-stage, command-and-control (C2) servers.” reads the published by Volexity. “The DNS records were poisoned to resolve to an attacker-controlled server in Hong Kong at IP address 103.96.130[.]107. Initially, Volexity suspected the initial victim organization’s firewall may have been compromised. However, further investigation revealed the DNS poisoning was not performed within the target infrastructure, but further upstream at the ISP level.”
Volexity promptly alerted the ISP, which then investigated key traffic-routing devices on their network. After rebooting and taking parts of the network offline, the DNS poisoning stopped. The researchers were not able to identify a specific compromised device, however, updating or deactivating various infrastructure components effectively ended the malicious activity.
“The logic behind the abuse of automatic updates is the same for all the applications: the legitimate application performs an HTTP request to retrieve a text-based file (the format varies) containing the latest application version and a link to the installer.” continues the report. “Since the attacker has control of the DNS responses for any given DNS name, they abuse this design, redirecting the HTTP request to a C2 server they control hosting a forged text file and a malicious installer. The AiTM workflow is shown below.”
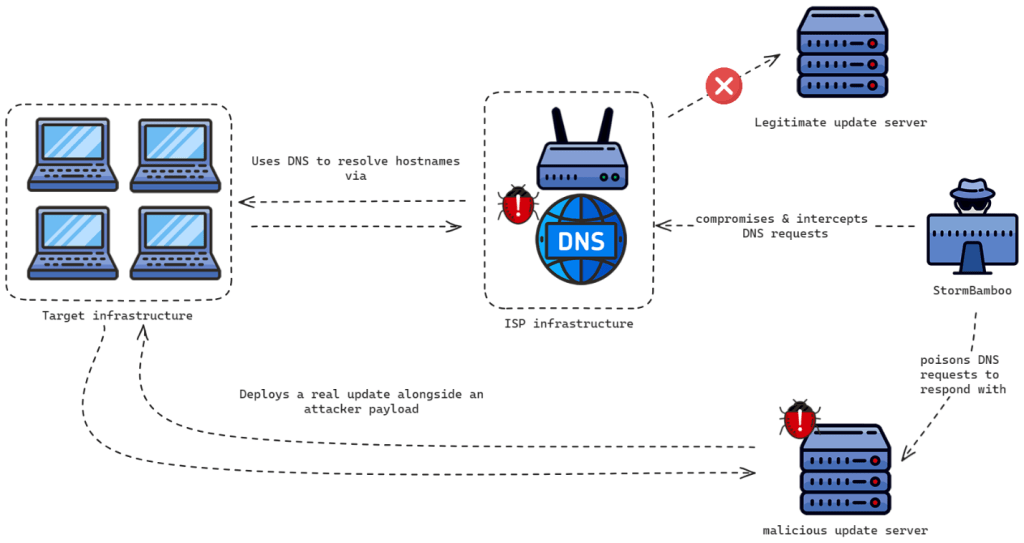
StormBamboo targeted various software vendors with insecure update mechanisms, using complex methods to deploy malware. For example, they targeted 5KPlayer’s update process for the “youtube-dl” dependency to deliver a backdoored installer from their C2 servers. Once compromised systems, the attackers installed a malicious Google Chrome extension called ReloadText to steal browser cookies and email data.
In June 2019, researchers at Cybereason uncovered an ongoing long-running espionage campaign, tracked as Operation Soft Cell, that targets telco providers. Tactics, techniques, and procedures, and the type of targets suggest the involvement of a nation-state actor likely linked to Chinese APT10.
Once compromised the networks of telecommunication companies, attackers can access to mobile phone users’ call data records.
“Based on the data available to us, Operation Soft Cell has been active since at least 2012, though some evidence suggests even earlier activity by the threat actor against telecommunications providers. The attack was aiming to obtain CDR records of a large telecommunications provider.” reads the published by Cybereason.
“The threat actor was attempting to steal all data stored in the active directory, compromising every single username and password in the organization, along with other personally identifiable information, billing data, call detail records, credentials, email servers, geo-location of users, and more.”
According to Amit Serper, head of security research at Cybereason, attackers exfiltrated gigabytes of data from the target networks, but always in relatively smaller amounts to remain under the radar.
In mid-September, Lumen’s Black Lotus Labs discovered a new botnet, named Raptor Train, composed of small office/home office (SOHO) and IoT devices. The experts believe the botnet is controlled by a Chine-linked APT group Flax Typhoon (also called Ethereal Panda or RedJuliett).
The botnet has been active since at least May 2020, reaching its peak with 60,000 compromised devices in June 2023.
Since May 2020, over 200,000 devices, including SOHO routers, NVR/DVR devices, NAS servers, and IP cameras, have been compromised and added to the Raptor Train botnet, making it one of the largest China-linked IoT botnets discovered. A command and control (C2) domain from a recent campaign even appeared on the Cloudflare Radar and Cisco Umbrella “top 1 million” lists, indicating widespread device exploitation. Researchers estimate that hundreds of thousands of devices have likely been compromised since the botnet’s creation.
China has consistently denied accusations from Western governments and tech firms about its involvement in cyberattacks. Liu Pengyu, a spokesman for the Chinese Embassy in Washington, recently accused U.S. spy agencies and cybersecurity firms of fabricating evidence to blame China. Despite these denials, China-linked APT groups have a history of targeting global telecommunications infrastructure.
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, Salt Typhoon)