
An APT group tracked as Void Banshee was spotted exploiting the Windows zero-day CVE-2024-38112 (CVSS score of 7.5) to execute code through the disabled Internet Explorer.
The vulnerability is a Windows MSHTML Platform Spoofing Vulnerability. Successful exploitation of this vulnerability requires an attacker to take additional actions before exploitation to prepare the target environment. An attacker can trigger the issue by sending the victim a malicious file that the victim would have to execute.
Trend Micro researchers discovered that the flaw was actively exploited in the wild in May and reported it to Microsoft which addressed the zero-day with the July 2024 Patch Tuesday security updates.
Void Banshee was observed exploiting the CVE-2024-38112 flaw to drop the Atlantida info-stealer on the victims’ machines. The malware allows operators to gather system information and steal sensitive data, such as passwords and cookies, from multiple applications.
In the group’s attack chain, Void Banshee attempts to trick victims into opening zip archives containing malicious files disguised as book PDFs. The archives are disseminated in cloud-sharing websites, Discord servers, and online libraries, and other means. The APT group focuses on North America, Europe, and Southeast Asia.
“This zero-day attack is a prime example of how unsupported Windows relics are an overlooked attack surface that can still be exploited by threat actors to infect unsuspecting users with ransomware, backdoors, or as a conduit for other kinds of malware.”
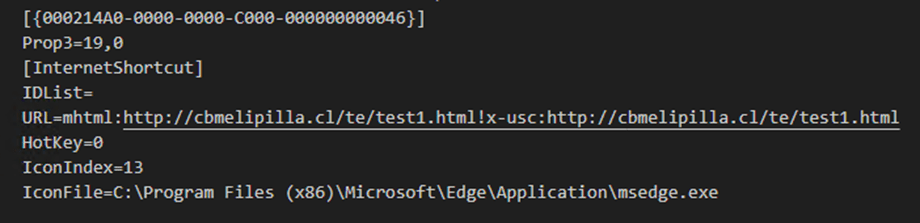
Void Banshee exploited the disabled Internet Explorer process to run HTML Application (HTA) files using specially crafted .URL files with the MHTML protocol handler and the x-usc! directive. This technique resembles the exploitation of CVE-2021-40444, another MSHTML flaw that was exploited in zero-day attacks. The experts warn that this attack method is very concerning because Internet Explorer no longer receives updates or security fixes.
“In this attack, CVE-2024-38112 was used as a zero-day to redirect a victim by opening and using the system-disabled IE to a compromised website which hosted a malicious HTML Application (HTA)” states the report. “In the URL parameter of the internet shortcut file, we can see that Void Banshee specifically crafted this URL string using the MHTML protocol handler along with the x-usc! directive. This logic string opens the URL target in the native Internet Explorer through the iexplore.exe process.”
Attackers used the internet shortcut file to direct the victims to an attacker-controlled domain where an HTML file downloads the HTA stage of the infection chain. The researchers noticed that Void Banshee uses this HTML file to control the window view size of Internet Explorer, hiding browser information and hiding the download of the next infection stage from the victim.
By default, IE prompts users to open or save the HTML application, but the APT group disguised the HTA file as a PDF by adding spaces to the file extension. Upon running the HTA file, a series of scripts is executed, along with the LoadToBadXml .NET trojan loader, the Donut shellcode, and the Atlantida stealer.
“In this campaign, we have observed that even though users may no longer be able to access IE, threat actors can still exploit lingering Windows relics like IE on their machine to infect users and organizations with ransomware, backdoors, or as a proxy to execute other strains of malware.” Trend Micro concludes. “The ability of APT groups like Void Banshee to exploit disabled services such as IE poses a significant threat to organizations worldwide. Since services such as IE have a large attack surface and no longer receive patches, it represents a serious security concern to Windows users.”
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, CVE-2024-38112)