
A threat actor is advertising a new ATM malware family that claims to be able of compromised 99% of devices in Europe. The threat actor is offering the malware for $30,000, he claims that the “EU ATM Malware” is designed from scratch and that can also target approximately 60% of ATMs worldwide.
If the claims are true, this malware poses a significant threat to the global banking industry. According to the announcement, the ATM malware can target machines manufactured by multiple leading vendors, including Diebold Nixdorf, Hyosung, Oki, Bank of America, NCR, GRG, and Hitachi.
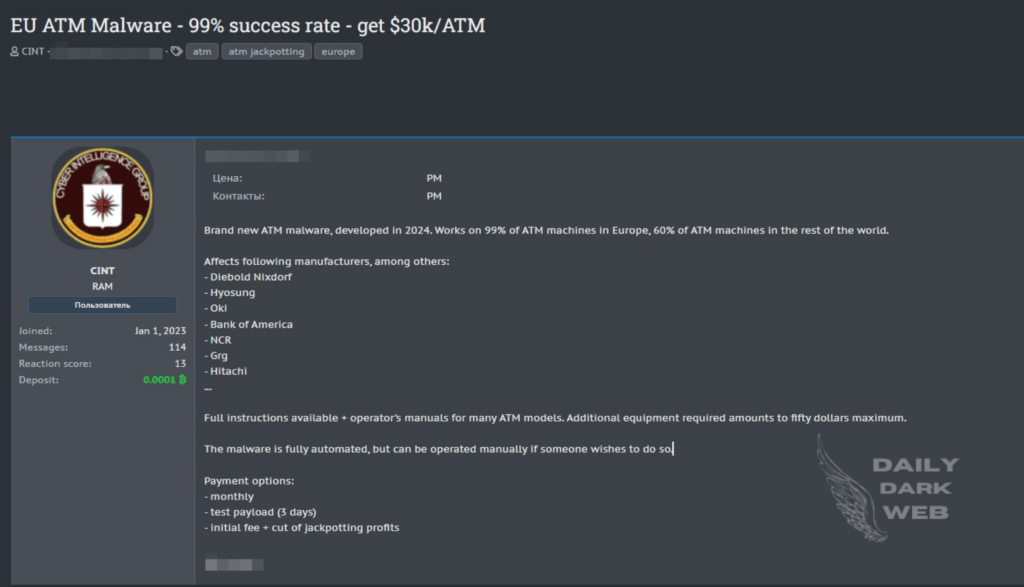
“The developers of this malware claim that it can generate up to $30,000 per ATM, making it a lucrative tool for cybercriminals.” . “The malware is fully automated, simplifying its deployment and operation.”
The malware is fully automated, making its deployment and operation straightforward and efficient, however, it also supports a manual operation mode.
The seller is offering the malware with multiple payment options, including a monthly subscription and an initial fee plus a share of the profits from successful jackpotting operations.
The threat actors also give customers a test payload option valid for three days.
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, malware)