
Microsoft researchers warned that multiple ransomware gangs are exploiting the recently patched vulnerability CVE-2024-37085 (CVSS score of 6.8) in VMware ESXi flaw.
“Microsoft researchers have uncovered a vulnerability in ESXi hypervisors being exploited by several ransomware operators to obtain full administrative permissions on domain-joined ESXi hypervisors.” Microsoft.
The flaw is an authentication bypass vulnerability in VMware ESXi.
“A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously by re-creating the configured AD group (‘ESXi Admins’ by default) after it was deleted from AD.” reads the published by the virtualization giant.
The company released patches for security vulnerabilities affecting ESXi 8.0 and VMware Cloud Foundation 5.x. However, no patches are planned for the older versions, ESXi 7.0 and VMware Cloud Foundation 4.x. Users of the unsupported versions are recommended to upgrade to newer versions to receive security updates and support.
Microsoft reported that multiple financially motivated groups like Storm-0506, Storm-1175, and Octo Tempest have already exploited this vulnerability to deploy ransomware.
“Microsoft security researchers identified a new post-compromise technique utilized by ransomware operators like Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest in numerous attacks.” continues Microsoft. “In several cases, the use of this technique has led to Akira and Black Basta ransomware deployments. “
Earlier this year, the Storm-0506 group breached an engineering firm in North America and deployed the Black Basta ransomware by exploiting the flaw CVE-2024-37085 to gain elevated privileges to the ESXi hypervisors.
“The threat actor gained initial access to the organization via Qakbot infection, followed by the exploitation of a Windows CLFS vulnerability (CVE-2023-28252) to elevate their privileges on affected devices. The threat actor then used Cobalt Strike and Pypykatz (a Python version of Mimikatz) to steal the credentials of two domain administrators and to move laterally to four domain controllers.” continues Microsoft.
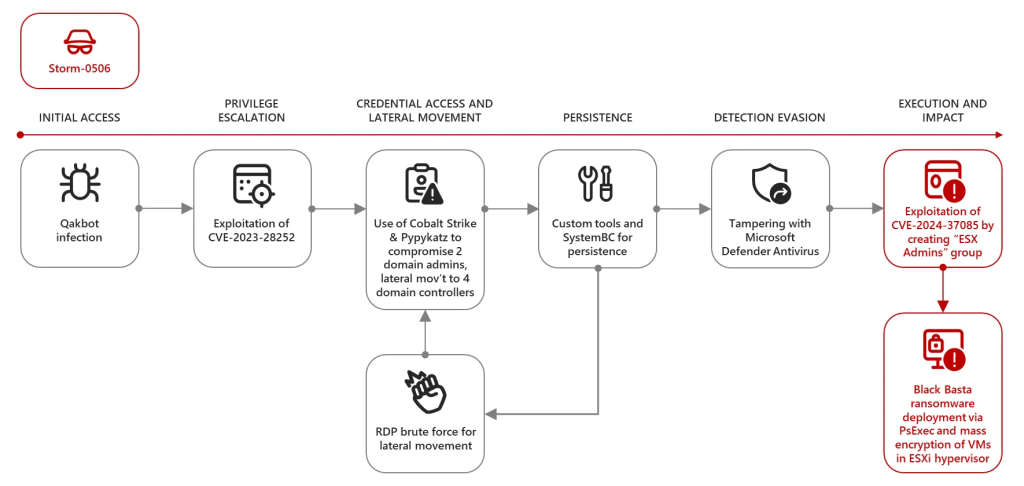
The attackers created the ‘ESX Admins’ group in the domain and added a new user account to it. The threat actors encrypted the ESXi file system and caused the lost of functionality of the hosted virtual machines on the ESXi hypervisor.
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, CVE-2024-37085)