
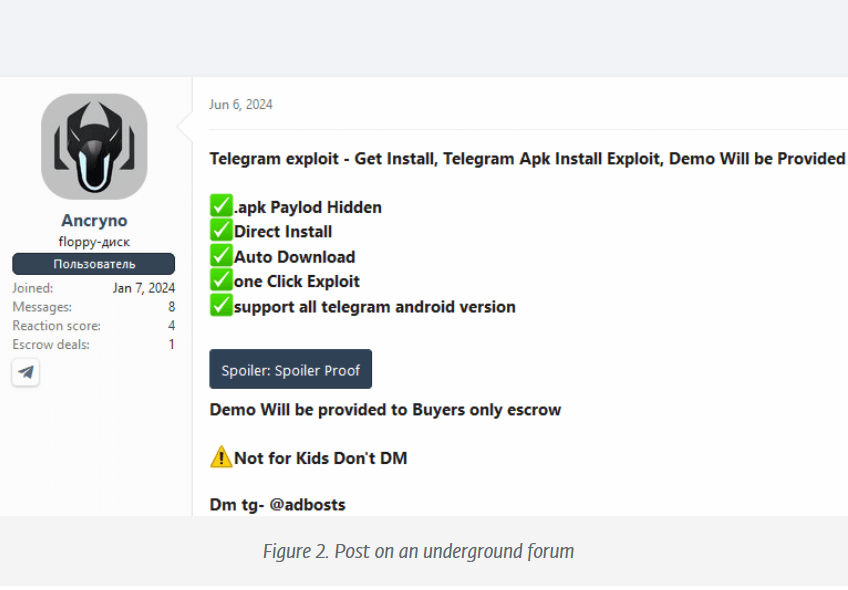
ESET researchers discovered a zero-day exploit named EvilVideo that targets the Telegram app for Android. The exploit was for sale on an underground forum from June 6, 2024, it allows attackers to share malicious Android payloads via Telegram, disguising them as multimedia files.
ESET researcher Lukas Stefanko reported the zero-day to Telegram on June 26 and later on July 4, 2024.
The exploit only works on Telegram versions 10.14.4 and older, the company addressed the flaw on July 11, 2024, with the release of versions 10.14.5 and above.
The seller, who uses the moniker ‘Ancryno,’ advertised the exploit on the XSS hacking forum. The seller showed screenshots and a video of testing the exploit on a public Telegram channel. ESET identified the Telegram channel, and obtained it
The exploit likely uses the Telegram API to upload specially crafted multimedia files, making the payload appear as a 30-second video rather than a binary attachment. Upon sharing in a chat the malicious payload appears like a video preview.
By default, Telegram automatically downloads media files, making users vulnerable to the EvilVideo exploit, which disguises malicious payloads as multimedia files. When attempting to play the fake video, Telegram suggests using an external player, leading users to install a malicious app. The exploit leverages a vulnerability in Telegram’s upload process to make the file appear as a video.
Below is the video PoC of the exploit:
ESET researchers tested the exploit on Telegram’s web client and Telegram Desktop and they discovered that the exploit doesn’t work because the payload is treated as an multimedia video file.
ESET has yet to determine if the exploit was used in attacks in the wild.
“We discovered a zero-day Telegram for Android exploit for sale on an underground forum. The vulnerability it exploits allows sending malicious payloads that look like multimedia files via Telegram chat. If a user tries to play the apparent video, they will receive a request to install an external app, which actually installs the malicious payload.” . “Luckily, the vulnerability has been fixed as of July 11th, 2024, after we reported it to Telegram.
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, zero-day)