
In late 2023, Sygnia researchers responded to an incident suffered by a large organization that they attributed to a China-linked threat actor tracked as ‘Velvet Ant.’
The cyberspies deployed custom malware on F5 BIG-IP appliances to gain persistent access to the internal network of the target organization and steal sensitive data.
The investigation revealed that the threat actor had been present in the organization’s on-premises network for about three years, aiming to maintain access for espionage purposes. They achieved persistence by establishing multiple footholds within the company’s environment. One method used was exploiting a legacy F5 BIG-IP appliance exposed to the internet, which served as an internal Command and Control (C&C). When one foothold was discovered and remediated, the threat actor quickly adapted and pivoted to another. This demonstrated their agility and deep understanding of the target’s network infrastructure.
The investigation revealed that the Chinese hackers had been present in the organization’s on-premises network for about three years. They achieved persistence by establishing multiple footholds within the company’s environment. One method used was exploiting a legacy internet-facing F5 BIG-IP appliance, which was also used by attackers as an internal Command and Control (C&C). After the researchers discovered and remediated one foothold, the APT group quickly pivoted to another. This demonstrated their agility and deep understanding of the target’s network infrastructure.
“The compromised organization had two F5 BIG-IP appliances which provided services such as firewall, WAF, load balancing and local traffic management. These appliances were directly exposed to the internet, and both of which were compromised. Both F5 appliances were running an outdated, vulnerable, operating system. The threat actor may have leveraged one of the vulnerabilities to gain remote access to the appliances.” reads the analysis published by Sygnia. “As a result, a backdoor hidden within the F5 appliance can evade detection from traditional log monitoring solutions.”
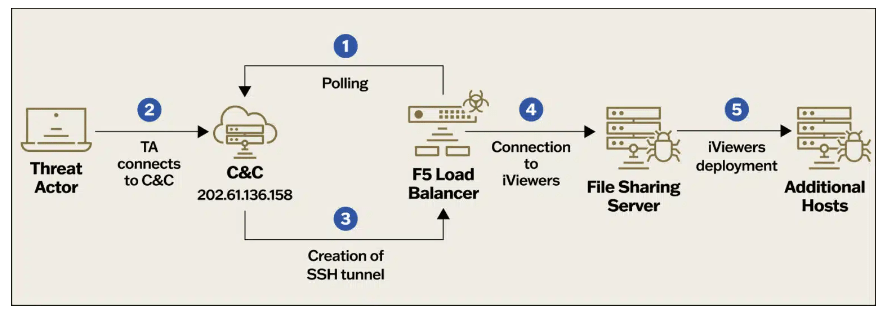
Once the attackers had compromised the F5 BIG-IP appliances, they gained access to internal file servers and deployed the PlugX RAT. The PlugX RAT was used by multiple Chinese APT groups in cyberespionage campaigns over the years.
Forensic analysis of the F5 appliances revealed that the Velvet Ant group also used the following malware in their attacks:
Researchers provided the following recommendations for organizations to mitigate attacks of groups like Velvet Ant:
The report also includes indicators of compromise for the attack analyzed by the researchers.
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, Velvet ANT APT)