
Researchers from cybersecurity firm GreyNoise have spotted exploitation attempts for the critical vulnerability CVE-2024-0769 (CVSS score 9.8) impacting all D-Link DIR-859 WiFi routers.
The vulnerability is a path traversal issue that can lead to information disclosure. Threat actors are exploiting the flaw to collect account information, including user passwords, from the vulnerable D-Link DIR-859 WiFi routers.
The vendor that the DIR-859 family of routers has reached their End of Life (“EOL”)/End of Service Life (“EOS”) life-cycle, and for this reason, the flaw will likely not be addressed.
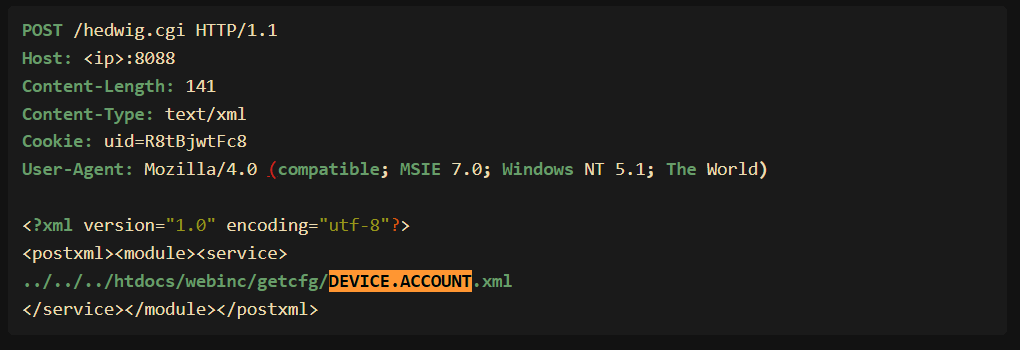
GreyNoise observed hackers targeting the ‘DEVICE.ACCOUNT.xml’ file to extract all account names, passwords, user groups, and user descriptions on the device. The attackers use a modified version of the public exploit.
“GreyNoise observed a slight variation in-the-wild which leverages the vulnerability to render a different PHP file to dump account names, passwords, groups, and descriptions for all users of the device. At the time of writing we are not aware of the motivations to disclose/collect this information and are actively monitoring it” reads the analysis published by GreyNoise.
“In the variation as observed by GreyNoise DEVICE.ACCOUNT.xml is utilized. We went ahead and retrieved this file in full. While the exploit conditions are the same as the public PoC, the variation as observed by GreyNoise is dumping all name, password, group, and description for all users of the device.”
The hackers are exploiting the flaw by sending a malicious POST request to ‘/hedwig.cgi,’ to access sensitive configuration files (‘getcfg’) via the ‘fatlady.php’ file, potentially leasing to the exposure of the user credentials.
Once the attackers have obtained the credentials, they can potentially take full control of the device.
“It is unclear at this time what the intended use of this disclosed information is, it should be noted that these devices will never receive a patch. Any information disclosed from the device will remain valuable to attackers for the lifetime of the device as long as it remains internet facing.” concludes GreyNoise. “These attributes make for the potential of a long-tail of exploitation that may come to a head at a later date, such as through a currently unknown authenticated RCE vulnerability in the affected device.”
The researchers pointed out that the public PoC exploit targets the ‘DHCPS6.BRIDGE-1.xml’ file instead of ‘DEVICE.ACCOUNT.xml’, for this reason, attackers can use it to attack other files.
The GreyNoise post include a list of possible variations of other getcfg files that can be invoked using CVE-2024-0769.
D-Link customers are recommended to replace the EoL devices as soon as possible.
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, D-Link DIR-859)