
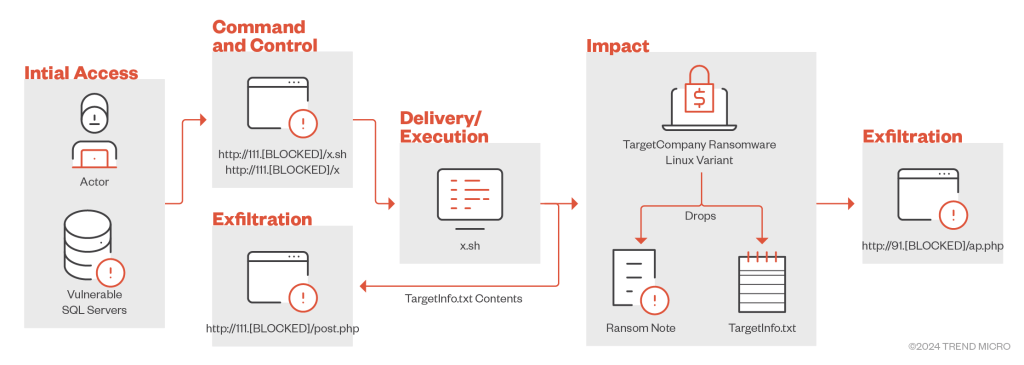
A new variant of the TargetCompany ransomware group uses a custom shell script as a means of payload delivery and execution, this is the first time the technique was observed in the wild.
The script was also used for data exfiltration, the stolen data are sent to two different servers so the ransomware actors have a backup of the information.
The new Linux-based variant was specifically designed to target VMWare ESXi environment.
has been active since , once encrypted a file it adds .mallox, .exploit, .architek, or .brg extension to the filenames of encrypted files.
Like other ransomware, TargetCompany removes shadow copies on all drives and kills some processes that may hold open valuable files, such as databases.
In February 2022, Czech cybersecurity software firm Avast released a decryption tool that could allow victims of the TargetCompany ransomware to recover their files for free under certain circumstances.
The threat actors behind TargetCompany are not targeting also virtualization environments to expand the scope of their attacks and cause greater damage and disruption. The ransomware operators have added the capability to detect if a machine is running in a VMWare ESXi environment by executing the “uname” command.
If the system name matches “vmkernel,” it indicates the machine is running VMware’s ESXi hypervisor. The malware then enters “VM mode” to encrypt files with specific extensions.
Once executed, the ransomware drops a text file named TargetInfo.txt that contains victim information. Like the Windows variant of the ransomware, the content of the file TargetInfo.txt is then sent to a C2 server.
Once the encryption process is completed, it drops a ransom note file named “HOW TO RECOVER !!.TXT” in all folders containing encrypted files. The malware appends the “.locked” extension to the encrypted filenames.
“The IP address used to deliver the payload and exfiltrate a victim’s system information has not yet been observed in previous TargetCompany campaigns. Based on research, this IP address is hosted by China Mobile Communications, an internet service provider (ISP) in China.” reads the published by Trend Micro. “The certificate also was recently registered and is valid for only three months, indicating that it might be intended for short-term use.”
Trend Micro linked the sample analyzed by its researchers to an affiliate named “vampire,” which was identified through data sent to its C2 server. The experts believe that larger campaigns with high ransom demands and extensive IT system targeting are ongoing. “Vampire” may be connected to an affiliate mentioned in a report published by Sekoia.
Malicious actors are continually enhancing their TTPs, as demonstrated by the emergence of TargetCompany’s new Linux variant. The lates development allows operators to broaden its range of potential victims by targeting VMware ESXi environments.
Trend Micro also published the indicators of compromise for this threat.
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, ransomware)