
Researchers at Fortinet FortiGuard Labs reported that threat actors exploited the recently disclosed OSGeo GeoServer GeoTools flaw (CVE-2024-36401) to deliver various malware families, including cryptocurrency miners, bots, and the SideWalk backdoor.
GeoServer is an open-source server that allows users to share and edit geospatial data.
GeoServer versions prior to 2.23.6, 2.24.4, and 2.25.2 are vulnerable to Remote Code Execution (RCE) due to unsafe evaluation of property names as XPath expressions. This issue arises because the GeoTools library API, which GeoServer uses, evaluates property/attribute names for feature types in a way that unsafely passes them to the commons-jxpath library, allowing arbitrary code execution. The vulnerability impacts all GeoServer instances, as it incorrectly applies XPath evaluation to simple feature types. An attacker can exploit the vulnerability through various requests such as WFS GetFeature, WFS GetPropertyValue, WMS GetMap, WMS GetFeatureInfo, WMS GetLegendGraphic, and WPS Execute requests. The vulnerability has been addressed in versions 2.23.6, 2.24.4, and 2.25.
In Mid-July, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the vulnerability to its .
According to Fortinet FortiGuard Labs, threat actors exploited the flaw to deliver the reverse proxy server GOREVERSE, which was used to establish a connection with a C2 server to gain access to the target systems.
The researchers observed threat actors exploiting CVE-2024-36401 in attacks aimed at IT service providers in India, technology companies in the U.S., government entities in Belgium, and telecommunications companies in Thailand and Brazil.
Other attacks observed by Fortinet exploiting the CVE-2024-36401 flaw involved the deployment of the advanced Linux backdoor SideWalk. The backdoor is attributed to the China-linked Winnti (aka APT41) cyberespionage group. The attack starts with a shell script that downloads binaries for various architectures (ARM, MIPS, X86), extracts a command-and-control (C2) server from an encrypted configuration, and connects to it. It also uses the legitimate tool Fast Reverse Proxy (FRP) to create an encrypted tunnel, enabling persistent remote access, data exfiltration, and further payload deployment while evading detection.
“Analysis of the script download URL’s telemetry reveals a concentrated pattern of infections. The primary targets appear to be distributed across three main regions: South America, Europe, and Asia.” the report. “This geographical spread suggests a sophisticated and far-reaching attack campaign, potentially exploiting vulnerabilities common to these diverse markets or targeting specific industries prevalent in these areas.”
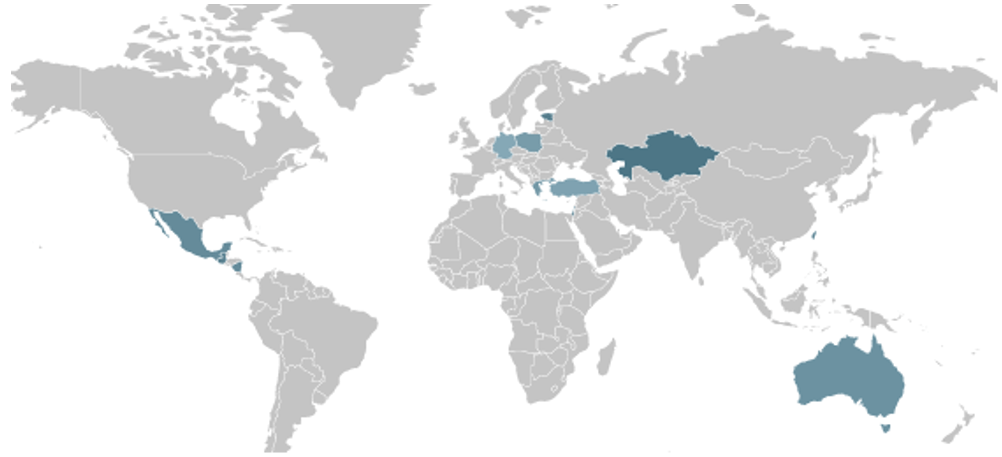
The flaw was also exploited to deliver Mirai Variant – JenX and the Condi DDoS bot. The experts reported that at least four types of coin miners were spreading exploiting the OSGeo GeoServer GeoTools flaw CVE-2024-36401.
“While GeoServer’s open-source nature offers flexibility and customization, it also necessitates vigilant security practices to address its vulnerabilities. The developer patched the vulnerability with the function “JXPathUtils.newSafeContext” instead of the original vulnerable one to evaluate the XPath expression safety.” concludes the report. “However, implementing comprehensive cybersecurity measures—such as regularly updating software, employing threat detection tools, and enforcing strict access controls—can significantly mitigate these risks. By”
Follow me on Twitter: and and Mastodon
(SecurityAffairs – hacking, malware)